Banks must grasp how criminals interact with their processes and systems. This allows upgraded security to defend customers.
Here’s how using the CEMMethod® to help
User Research and Real Events.
- Study actual fraud cases.
- See how criminals use bank offerings.
- Document fraudster actions, steps taken, what they engaged with, and victim emotions.
- Consider both failed and successful crimes for a complete view.
Chart Fraudster Customer Journeys.
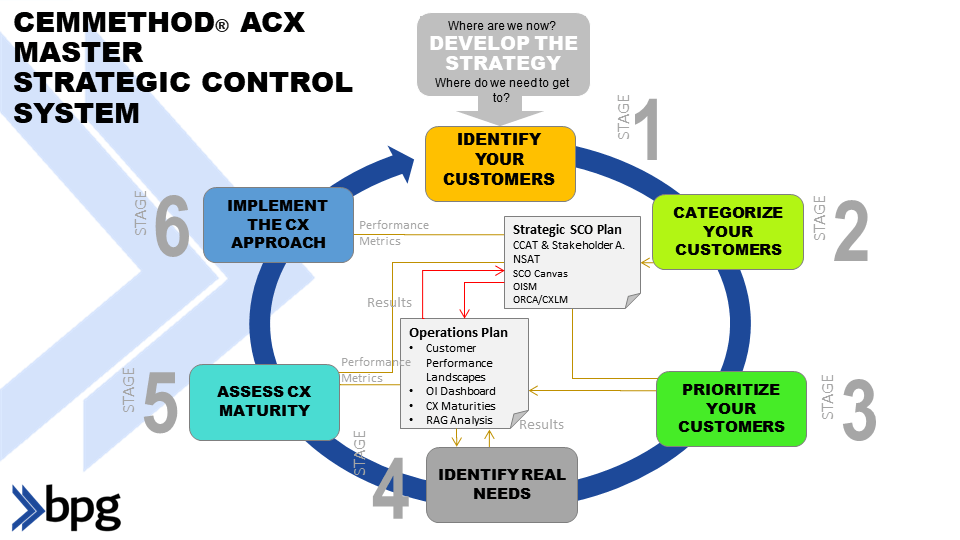
- Use the Outside-In Strategic Matrix (OISM), but initially focus just on fraudsters.
- Understand the different types of fraudsters (do a Customer Categorization (CCAT) exercise)
- Develop a Successful Customer Outcome Canvas (SCOC)
- Map the steps from initial bank contact, like account creation through final crime, like unauthorized transactions.
- Calculate the Disruption Factor (DF)
- Use the Innovation approach to identify Moments of Truth (MOTs), weak points, and areas for improvement within this path.
- Based on the Innovation approach recalculate the DF to show the improvement
Note Every Interaction and Channel.
- Account for all criminal bank MOTs/touchpoints, including:
- Account creationLogin/authentication
- Transaction history
- Phone, email, and chat communications
- Customer support exchanges
See how criminals exploit weaknesses at each step.
- Complete a Risk-Impact matrix (RIM)
Data is Key Over Visuals.
- Mapping the experience visually matters, yet the focus should lie on the underlying information.
- Comprehend patterns, triggers, and behavioural signals.
- Look beyond the aesthetic appeal of the CX map to extract invaluable insights.
Customer Viewpoint and Emotions.
- Step into a fraudster’s shoes. Use the ‘empty chair approach’.
- What drives them? What emotions arise?
- Also, empathize with legitimate customers who fall prey to fraud.
- Understand their feelings of anxiety, frustration, and vulnerability.
Cross-Team Collaboration.
- Involve teams spanning fraud prevention, UX design, security experts, and customer support.
- Share insights, collaborating to address vulnerabilities identified in the fraudster’s journey.
Prioritizing Account Takeover (ATO).
- Recognize fraudsters directly target user accounts.
- Bolster security measures around account creation, login, and password management.
- Educate users on secure practices to prevent ATO.
Adapting to Evolving Trends.
- Stay informed about shifting fraud tactics.
- As fraudsters adapt, so must your defences.
- Monitor phishing, social engineering, and other fraudster methods.
Balancing Security and User Experience.
- You should enhance security without hindering genuine users.
- Make sure the security upgrades don’t negatively affect user experience.
- Put security measures smoothly, no hassle for real customers.
Keep Improving.
- Review the fraudster’s plan often, update CX map regularly.
- Revisit the OISM and CCAT and update them on a regular basis
- Try new checks, and analyze if they work well against threats.
- Learn from actual incidents and modify practices accordingly.
Frequently Asked Questions Related Bank Fraud and the CEMMethod®
Frequently Asked Questions Related to Bank Fraud and the CEMMethod®
- What is CEMMethod®? How does the CEMMethod® help? The CEMMethod® is a comprehensive approach that aims to improve customer experiences by aligning all aspects of an organization with customer needs and experiences.
It helps by:
> Lowering costs, increasing revenues, and improving service through the Triple Crown approach.
> Utilizing tools like the Successful Customer Outcome Canvas (SCOC) and the Outside-In Strategic Matrix (OISM) to identify and prioritize key customer outcomes. - Implementation Challenges: Common challenges banks face when implementing the CEMMethod® for fraud prevention include:
> Integrating the method with existing processes and systems in a way that is both effective and efficient.
> Ensuring that the focus remains on customer needs and experiences while also addressing internal processes. - Measuring Success: Banks measure the success and effectiveness of the CEMMethod® in fraud prevention by:
> Assessing the impact on key outcomes such as lower costs, higher revenues, and improved service.
> Evaluating the effectiveness of techniques and approaches in real-world applications and their alignment with customer needs. - Integration with Existing Systems: The CEMMethod® can be integrated with existing bank systems and processes for seamless fraud prevention by:
> Aligning with technologies such as AI, digitization, and machine learning for significant cost reductions and revenue uplift.
> Adapting the portfolio of techniques and approaches to suit all circumstances, ensuring rigorous dashboards focused Outside-In.
For more detailed information and practical applications, you can explore the resources and guides available on the CEMMethod®

Steve Towers, BPG’s Chief Experience Officer, is an expert in customer experience and process transformation who enjoys spreading his enthusiasm for this field through coaching, consultancy, keynote talks and books (twelve published).
Through the CEMMethod®, now in version 15, he and the BPG affiliates help companies win the triple crown 👑 —the simultaneous ability to Grow Revenue, Reduce Costs, and Improve service.
With over four decades of experience working with large enterprises worldwide, Steve has distilled the successful strategies of top-performing organizations into a proprietary methodology that can be easily imparted to CX and Process teams and executives.
His forte lies in envisioning the future of customer-centricity, customer experience, process management and realizing long-term benefits from business transformation. Steve’s approach combines customer-focused thinking, cutting-edge technologies, and a human touch.
Steve is also an entrepreneur and an early-stage investor in innovative software companies.
Subscribe to this channel and reach out and connect with Steve via https://linktr.ee/stevetowers